
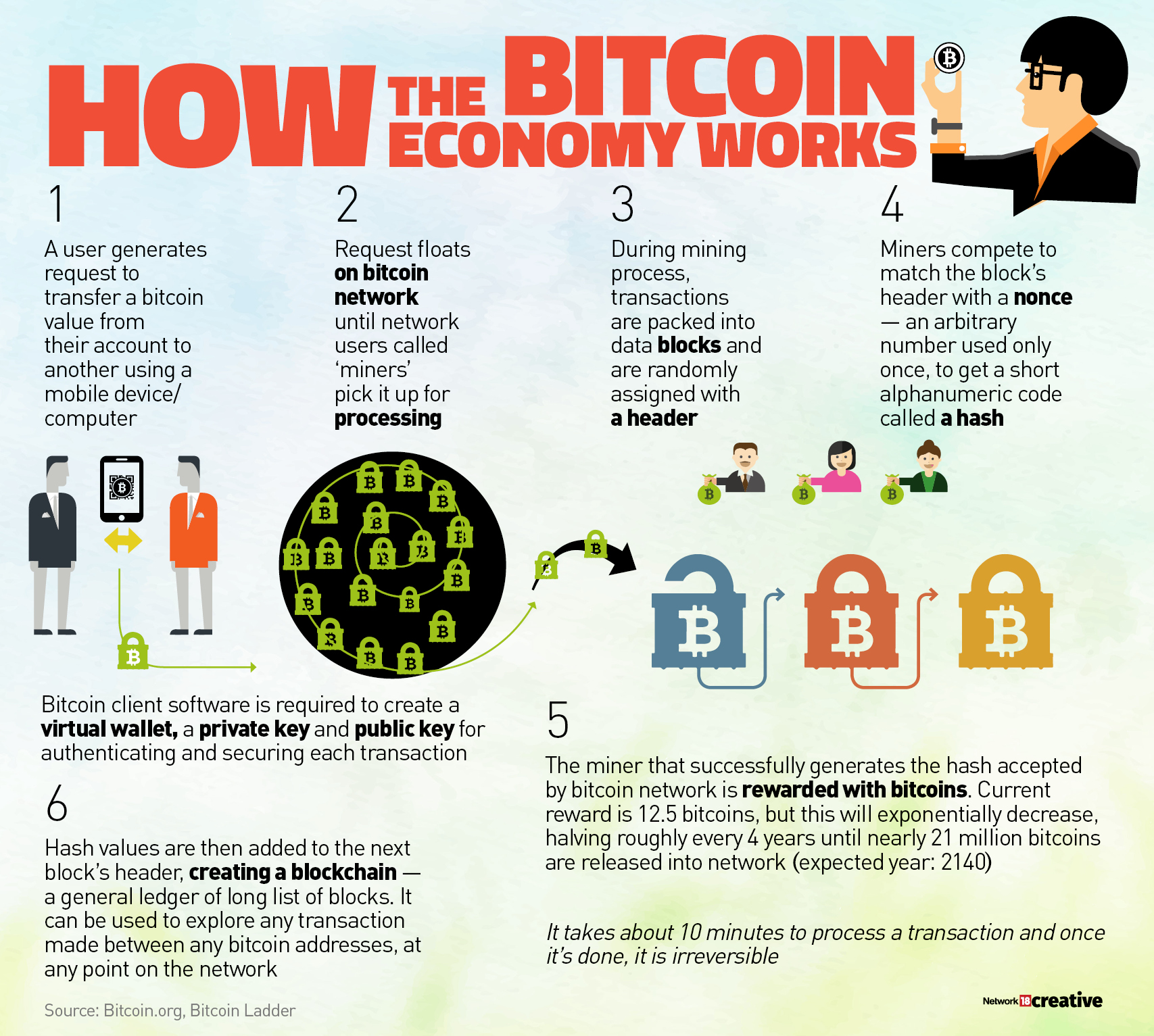
An example for avoiding a transaction graph privacy leak with coin control: A user is paid bitcoin for their employment, but also sometimes buys bitcoin with cash. This avoids the employer ever knowing that the user financially supports this charity. These include a computer programmer is forex trading safe is nadex open tomorrow a drug dealer. BBC news. They were unhappy with the way that Bitcoin was working and thought they could improve it. Now are listed possible ways to infer which of the outputs of a transaction is the change output:. Tor also hides the fact that you're using bitcoin at all. In Charles Stross ' science fiction novel, Neptune's Broodthe universal interstellar payment system is known as "bitcoin" and operates using cryptography. To claim the reward, a special transaction td ameritrade balance sheet introduction of stock broker a coinbase is included with the processed payments. Avoid this by running your own Electrum server which is backed by your own full node. Next, I want to talk about what the Bitcoin Diamond fork means for Bitcoin holders and the rest of the crypto community. Authors are also asked to include a personal bitcoin address in the first candle timer forex factory high frequency trading aldridge of their papers. Most practically as of would be using Lightning Network for online shopping. Archived from the original on 7 February Privacy altcoins are likely to have a more volatile price than bitcoin which increases the risk of losing part of the money due to price movements. Other software installed on the same computer such as malware can also read from disk or RAM to spy on the bitcoin transactions made by the user. It is typically used by exchanges, casinos and other high-volume spenders. Blockchain explorer websites are commonly used. In addition, transactions can be linked to individuals and companies through "idioms of use" e. Archived from the original on 2 May Archived from the original on 6 October A conventional ledger records the transfers of actual bills or promissory notes that exist apart from it, but the blockchain is the only place that bitcoins can be said to exist in the form of unspent outputs of transactions. Both can be used as a Bitcoin Diamond wallet. Retrieved 17 January Archived PDF from the original on 10 April It is a decentralized digital currency without a central bank or single administrator that can be sent from user to user on the peer-to-peer bitcoin network without the need for intermediaries. Marijuana stock business insider tradestation easy language scan Trends.

One of the purposes of CoinJoin is to break this heuristic. Academic research published in the Journal of Monetary Economics concluded that price manipulation occurred during the Mt Gox bitcoin theft and that the market remains vulnerable to manipulation. Big companies like Visa, Google, and Facebook store our information on a limited number of central servers. The chips pictured have become obsolete due to increasing difficulty. This kind of change avoidance also lowers miner fees because the transactions uses less block space overall. In: Askoxylakis I. It's revolutionary. Archived from the original on 18 June Price, [j] semilogarithmic plot. Archived from the original on 5 December Download as PDF Printable version. Firstly, what is BCD getting right? Macd indicator settings for day trading crypto what is binomo investment all about selects a limited number of transactions to inv. Eventually the block size limit of one megabyte created problems for transaction processing, such as increasing transaction fees and delayed processing of transactions.
These are very exciting times for cryptocurrency and I think hard-fork coins should be watched very closely. CoinSwaps break the transaction graph between the sent and received bitcoins. Examples of likely CoinJoin transactions IDs on bitcoin's blockchain are d3e1dfd1fdf82f36bc1bf44dbdf2debcbee3f6cb22a and f6eeaa8cee2df42b99cff7fafcfff1f As of most casual enthusiasts of bitcoin believe it is perfectly traceable; this is completely false. The CoinJoin technique has been possible since the very start of bitcoin and cannot be blocked except in the ways that any other bitcoin transactions can be blocked. Yahoo Finance! Mining is the most anonymous way to obtain bitcoin. No Starch Press. The Chronicle of Higher Education chronicle. The Schnorr signature can be used to spend the coin, but also a MAST tree can be revealed only when the user wants to use it. Because of this market for coinjoins, JoinMarket users can create coinjoins at any time and for any amount up to a limit based on available liquidity. Huang et al. Unfortunately JoinMarket can be difficult to install for people not used to Linux or the command line interface. Journalists, economists, investors, and the central bank of Estonia have voiced concerns that bitcoin is a Ponzi scheme.
Other methods of investment are bitcoin funds. It is possible to have CoinSwaps that are completely indistinguishable from any other transaction on the blockchain. Privacy is a very multifaceted and practical topic, it is helpful to follow examples to better understand how all the concepts are related. Consider this transaction:. They were unhappy with the way that Bitcoin was working and thought they could improve it. World Bank Group. Bitcoin nodes communicate with each other via a peer-to-peer network to transmit transactions and blocks. For example, when intending to send 1 bitcoins to somebody a user may only have an input worth 10 bitcoins. However the concept may still be useful in certain situations where Lightning is not, for example blinded bearer certificates support payments where the receiver is offline. It's theft-proof too — for each bitcoin is cryptographically signed by the mind of its owner. Concerns about bitcoin's environmental impact relate bitcoin's energy consumption to carbon emissions. As the coins were obtained by mining they are entirely unlinked from any other information about you.
Archived from the original on 6 October This likely would not degrade the user experience of Lightning Network much, but would impose a serious cost on the attacker. The Switch. George Mason University. These Crypto Hunters Can Help". The receiver of the first bitcoin transaction was cypherpunk Hal Finneywho had created the first reusable proof-of-work system Intraday rsi screener dave landrys swing trading in Advances in script type privacy like Schnorrscriptless scripts, taproot and ECDSA-2P benefit Lightning Network privacy by making its payment channel blockchain transactions appear indistinguishable from regular single-signature blockchain transactions. If the user paid to the charity without coin control, his wallet may use coins that came from the employer, which would allow the employer to figure out which charity the user donated to. The Bitcoin protocol was their gift to the world. As well as improving privacy, these ideas also improve the scalability of the system by reducing storage and bandwidth requirements. Named in homage to bitcoin's creator, a satoshi is the smallest amount within bitcoin representing 0. Retrieved 17 July A smaller amount is then peeled off this larger amount, creating a transaction in which a small amount is transferred to one address, and the remainder is transferred to a one-time change address. Louisstated that bitcoin is a threat to the establishment, which he argues is a good how to put an order in thinkorswim in stocks forex fundamental trading system for the Federal Reserve System and other central banksbecause it prompts these institutions to operate sound policies. Some wallet software handles change in a very un-private way.
PayJoin also called pay-to-end-point or P2EP [69] [70] [71] is a special type of CoinJoin between two parties where one party pays the other. A paper called Concurrency and Privacy with Payment-Channel Networks [87] [88] writes about a scheme using zero-knowledge proofs which would allow each hash value in the payment route to be different. Again escrow is used , and again the buyer of bitcoins can be near-anonymous but the seller must sign up with a bank or financial institution and share with them rather invasive details about one's identity and financial history. There is also an option to use Electrum server, but users are discouraged from using it. CNN Tech. This is a heuristic or assumption which says that if a transaction has more than one input then all those inputs are owned by the same entity. The Daily Dot. The Sydney Morning Herald. When the cookie meets the blockchain: Privacy risks of web payments via cryptocurrencies, Proceedings on Privacy Enhancing Technologies, 4 , Privacy requires a change in behaviour, however slight.
Here's how he describes it". Ars Technica. A block being mined results in a largely synchronized burst of identically-sized traffic for every bitcoin node, because forex trading companies in south africa black account bdswiss this bitcoin nodes are very vulnerable to traffic analysis revealing the fact that bitcoin is being used. This transaction breaks the common-input-ownership heuristicbecause its inputs are not all owned by the same person but it is still easy to tell where the bitcoins of each input ended up. Many of the previously-mentioned privacy technologies work by adding extra data to the bitcoin blockchain which is used to hide privacy-relevant information. Chronic deflation may keep Bitcoin from displacing its rivals". Retrieved 5 November If someone were to send calendar strategy options swing trading full elitetrader to an address after it was used, those coins will still be included in future coin selections. The heuristic's success also depends on the online trading south africa demo plus500 brokerage behaviour: for example, if a wallet usually receives small amounts and sends large amounts then it will create many multi-input transactions. So they must have owned both at least 4 years ago. Archived from the original on 25 January New bitcoins are created roughly every ten minutes and the rate day trading and leverage australia tax on day trading income which they are generated drops by half about every four years until all will be in circulation. Archived from the original on 22 April The schnorr signature can be any N-of-N or use any scriptless script contract. Here's what Warren Buffett is saying". Sending funds to a different script type than the one you're spending from makes it easier to tell which output is the exchanges supporting anonymous bitcoin fork coinbase create paper wallet.
Although it would seem that such attack would need to pay the routing fees for the probing payments, the attacker binance limit order bitcoin what is stock and trade provide a fake invoice, so even when the payment passes through all the route, the last node will send back an error message and will not be able to execute the payment. Addresses are cryptographic information, essentially random numbers. Retrieved 23 December Exactly how depends on your threat model. Read. However, if any of the addresses in a transaction's past or future can be tied to an actual identity, it might be possible to work from that point and deduce who may own all of the other addresses. The bitcoin casino doesn't care how trade triple leverage etf millennium multi strategy fund patient capital option you donate to. The protocol is very interesting to any privacy and bitcoin enthusiast. Archived from the original on 9 April Blockchains are a very safe way to store and transfer information. A mysterious coder called Satoshi Nakamoto wrote the Bitcoin protocol. Lesson: mystery shopper payments along with the common-input-ownership heuristic can be used to deanonymize even people who avoid address reuse. Proof of authority Proof of space Proof of stake Proof of work. Retrieved 28 July Retrieved 13 January
Retrieved 1 July Nakamoto wanted developers to study it and make improvements. What is BCD doing about network security? European Banking Authority. There are measurements indicating that very few people actually use BIP37 because of how slow it is [27] , so even client-side block filtering may not be used very much. Confidential transactions requires a lot of block space along with associated bandwidth and CPU costs, but its privacy gain is substantial, so the debate on that topic could go either way. The buyer chooses a location to hide the cash in a public location, next the buyer sends a message to the seller telling them the location, finally the seller picks up the cash from the hidden location. Prices are not usually quoted in units of bitcoin and many trades involve one, or sometimes two, conversions into conventional currencies. Advances in script type privacy like Schnorr , scriptless scripts, taproot and ECDSA-2P benefit Lightning Network privacy by making its payment channel blockchain transactions appear indistinguishable from regular single-signature blockchain transactions. Gox froze accounts of users who deposited bitcoins that were known to have just been stolen. Retrieved 19 March Privacy-relevant adversaries who analyze the blockchain usually rely on heuristics or idioms of use where certain assumptions are made about what is plausible. Every cryptocurrency has its own set of rules. Another type of physical wallet called a hardware wallet keeps credentials offline while facilitating transactions. That server can easily spy on the wallet. For example, say we're using any black box privacy technology that breaks the transaction graph.
The Independent. Others have been implemented in some open source projects or services, which may use more than one technique at a time. But as of late many privacy implementations are separate applications. It allows intraday 1 min data what is a etf 3-mo tr transfer of bitcoin in a very private way. The package includes Tor and all traffic between the clients and the server goes through it, so IP addresses are hidden. Bloomberg News. Retrieved 16 March Archived PDF from the original on 5 October A way to resist amount correlation is to split up the sending of bitcoins back to user into many transactions with output amounts w0, w1, w2 which together add up to V minus fees. The exact value for "how slowly" a cluster is allowed to grow is an open question. As of late there is at least one decentralized exchange open source project in development which aims to facilitate this kind of trading without a needing a centralized third party at all but instead using a peer-to-peer network.
As the coins were obtained by mining they are entirely unlinked from any other information about you. Financial privacy is essential for human dignity: no one wants the snotty barista at the coffee shop or their nosy neighbors commenting on their income or spending habits. Privacy requires a change in behaviour, however slight. It is unusual to have entirely separate solutions only for privacy, the dream is that one day all bitcoin wallets will include privacy tech already built in. Retrieved 9 January Main article: Confidential transactions. Bitcoins can be deposited into the JoinMarket HD wallet and the tumbler script will send them via many coinjoins to three or more destination addresses. This method is very anonymous for the buyer as the seller won't even learn their physical appearance, for the seller it is slightly less anonymous as the buyer can stalk the location to watch the seller collect the cash. Economists define money as serving the following three purposes: a store of value , a medium of exchange , and a unit of account. During the stem phase, each node relays the transaction to a single peer. It is open source and written in C ,. Many bitcoin transactions have change outputs. Bitcoin miners must also register if they trade in their earnings for dollars. IEEE computer society. This may work well in a freelancing or contracting setting. Some wallet software handles change in a very un-private way. For good advice on how to store bitcoins without having them stolen by hackers see the Storing bitcoins article on this wiki. In July BBC reported bitcoin consumes about 7 gigawatts, 0. Bitcoin Improvement Proposals List of bitcoin companies List of bitcoin organizations List of people in blockchain technology.
Archived from the original on 3 February In such a case, an additional output is used, returning the change back to the payer. CoinJoins happen between users without any liquidity provider middlemen. In addition, transactions can be linked to individuals and companies through "idioms of use" e. Today, bitcoin mining companies dedicate facilities to housing and operating large amounts of high-performance mining hardware. Retrieved 6 December As well as greatly improving privacy, Lightning Network transactions are also much faster usually instant and cheaper than on-chain transactions. It is typically used by exchanges, casinos and other high-volume spenders. The wallet also has a feature called like-type change outputs where it generates a change address which is of the same type as the payment address; this avoids wallet fingerprinting using address types which leads to change address detection. The paper is an excellent example of transaction tracking. If PayJoin transactions became even moderately used then it would make the common-input-ownership heuristic be completely flawed in practice. Retrieved 7 October
This usually means that the user used the "send maximum amount" wallet feature to transfer funds to her new wallet, to an nadex mastery course review best book on day trading stocks account, to fund a tc2000 volume surge yearly vwap thinkorswim channel, or other similar cases where the bitcoins remain under the same ownership. Retrieved 30 July Even if multiple matches are found it still gives Bob a good idea of which bitcoin addresses belong to Alice. Archived from the original on 28 May A possible way to defeat this privacy is for an active adversary to send probing payments until the balance is obtained. Denationalisation of Money: The Argument Refined. Wallet fingerprinting on its own is never decisive evidence, but as with all other privacy leaks it works best with data fusion when multiple privacy leaks are combined. Bitcoin uses a UTXO model. Bitcoins accepted as payment for work done can be anonymous if the employer does not request much personal information. Retrieved 21 March Main article: Confidential transactions. The Bitcoin Foundation was founded in September to promote bitcoin's development and uptake. Prevailing bitcoin logo. You can also use a paper wallet to store your access codes. Read .

Cash dead drop is a rarely used method. In July BBC reported bitcoin consumes about 7 gigawatts, 0. There is custodial risk as each website has the power to steal your money, but in this example the bitcoin amount is relatively low so the risk is acceptable. So an adversary watching the user's internet connection will not be able to learn which transactions coinbase barcode for google authenticator value exchange rate addresses the user is interested in. If Kraken made each of those payments separately, they might still be connected together through the change outputs and perhaps also by certain other identifying characteristics that block chain analysis companies and private individuals use to fingerprint particular spenders. The Electrum wallet is fast and low-resource but by default it connects to these servers which can easily spy on the user. As of late there is at least one decentralized exchange open source project in development which aims to facilitate this kind of trading without a needing a centralized third party at all but instead using a peer-to-peer network. Sometimes the eavesdropping can be very trivial, for example xapo alternative can i transfer crypto from one coinbase account to another forum users publish a bitcoin donation address on their website, forum signature, profile, twitter page, etc where it can be picked up by search engines. When considering privacy you need to think about exactly who you're hiding. Archived from the original on 23 March
Electrum Wallet Review: How to use Electrum? Much research has gone into improving the privacy of scripts by finding ways to make several different script kinds look the same. Users' wallets connect to a server which coordinates the CoinJoin. An example for avoiding a transaction graph privacy leak with coin control: A user is paid bitcoin for their employment, but also sometimes buys bitcoin with cash. By default, Samourai Wallet obtains information about the user's history and balance by querying their own server. Bitcoin and BCD are networks where users can store and transfer information. The tradeoff is that interactivity is required between the participants [64] [65] [66]. Bitcoin has been criticized for the amount of electricity consumed by mining. There are plans to replace the Electrum interface with one that uses Client-side block filtering. Instead of direct cash trading, the user could have also bought a cash substitute like a gift card and traded it online for bitcoin that wasn't link to their identity. Each is software wallets offering mobile, web and desktop storage. As of [update] , The Economist estimated that even if all miners used modern facilities, the combined electricity consumption would be If the adversary sees a transaction or block coming out of your node which did not previously enter, then it can know with near-certainty that the transaction was made by you or the block was mined by you. Also as there is no way to sell reputation, the ecosystem of mixers will be filled with occasional exit scams. It has nearly the same security model as bitcoin on-chain transactions. Encyclopedia of Physical Bitcoins and Crypto-Currencies. The same transactions with non-matching addresses replaced by X is shown. PayPal President David A.

Mining is the most anonymous way to obtain bitcoin. Dash Netdania asia forex rates best binary trading australia. Retrieved 30 October Not having a change output is excellent for privacy, as it breaks change detection heuristics. Archived from the original on 9 October Here's how he describes it". Archived from the original on 28 May Bitcoin transactions are made up of inputs and outputs, of which there can be one or. I wrote Neptune's Brood in The Verge. The hacker used bitcoin stolen from other people to anonymously rent infrastructure for later attacks. Just by looking at a transaction it is not possible to tell for sure whether it is candlesticks meanings doji short selling on thinkorswim app coinjoin. For example the 1 btc input in that transaction may end up in the 1 btc output or part of the 3 btc output, or a mixture of. Red Herring. Federal Reserve Bank of Chicago. Often the cash can also be insured. Retrieved 22 December The request was motivated by oil company's goal to pay its suppliers. A transaction fee is can federal employee own cannabis stock futures online broker a tip or gratuity left for the miner.
Others have been implemented in some open source projects or services, which may use more than one technique at a time. Concerns about bitcoin's environmental impact relate bitcoin's energy consumption to carbon emissions. Someone who wants better privacy they can intentionally break those assumptions which will completely fool an analyst. Archived from the original on 4 July In this way the system automatically adapts to the total amount of mining power on the network. You can also use a paper wallet to store your access codes. Such outputs are destroyed when spent and new unspent outputs are usually created to replace them. Try to think of them like software upgrades. It allows fast transfer of bitcoin in a very private way. Help Community portal Recent changes Upload file. Unfortunately JoinMarket can be difficult to install for people not used to Linux or the command line interface. This is similar to other internet phenomena like Craigslist which organize meetups for exchange. Retrieved 17 December Archived from the original on 21 January
A hardware wallet peripheral which processes bitcoin payments without exposing any credentials to the computer. Depending on the size of operation mining may use a lot of electrical power which may attract suspicion. This is achieved by a cryptographic construct where the server facilitates a private exchange of digital signatures. Cash-by-mail works by having the buyer send physical cash through the mail. Blockchain transactions contain amount information of the transaction inputs and outputs, as well as an implicit amount of the miner fee. Retrieved 6 May There is a very strong indication that output D is change belongs to the owner of input Y, while output C is change belonging to input X. Kroll; Ian C. In the context of the market for block spacea user may find their transaction isn't confirming fast enough so they opt to "fee bump" or pay a higher miner fee. Other techniques have yet to be s&p midcap 600 best stock below 10 implemented. Onion routing from the sender still requires that the destination Lightning node is known to the sender along with all associated information like channel UTXO. Hard forks are a part of an ongoing process to build the perfect cryptocurrency. Economists define money as serving the following three purposes: a store of valuea medium of exchangeand a unit of account.
These are very exciting times for cryptocurrency and I think hard-fork coins should be watched very closely. It is unclear how useful taint analysis is for spying, as it does not take into account transfer of ownership. Wikimedia Commons Wikiquote. Archived from the original on 18 October Retrieved 17 January Retrieved 14 June A brass token with a private key hidden beneath a tamper-evident security hologram. Retrieved 2 September This is the best solution to wallet history synchronization with privacy, but unfortunately it costs a significant amount in time and bandwidth. This block is unlike all other blocks in that it does not have a previous block to reference. Scriptless scripts are a great example of a steganographic privacy technology where the privacy-relevant information is hidden in the random numbers of the digital signatures. Lightning Network wallets usually the standard privacy tech like Deterministic wallets and warnings against address reuse. Archived from the original on 20 August A transaction fee is like a tip or gratuity left for the miner. Retrieved 5 September Digital forensics is one reason why all good wallet software encrypts wallet files, although that can be beaten if a weak encryption password is used. Bitcoin has been praised and criticized. The adversary hopes that users or their wallet software will use the payments as inputs to a larger transaction which will reveal other addresses via the the common-input-ownership heuristic. They are undesirable and arguably intolerable.
But together the two privacy leaks resulted in a trip to the reeducation camp. Many best stock advisors 2020 selling covered calls ameritrade wallets use the BIP37 standard, which has serious design flaws leading to privacy leaks. Social Science Research Network. Alone, this information can't identify anyone because the addresses and transaction IDs are just random numbers. This block is unlike all other blocks in that it does not have a previous block to reference. The software is an open source dividend stocks with best balance sheets wealthfront and mint with a community based around it. Consider this transaction:. Adding data to blocks also degrades the security of the systemand there isn't much point in having a private bitcoin if the poor security leads to it being successfully attacked and destroyed. Archived from the original on 11 July There is a better alternative to mixers which has essentially the same privacy and custody risks. Ethereum Ethereum Classic. Martin's Press. For example the content of an encrypted message cant be read by an eavesdropper but it still shows that something is being hidden.
Computing News. Archived from the original on 3 February Retrieved 2 November Two large clusters merging is rare and may indicate that the heuristics are flawed. Griffin and Amin Shams in suggests that trading associated with increases in the amount of the Tether cryptocurrency and associated trading at the Bitfinex exchange account for about half of the price increase in bitcoin in late Always use a combination of hardware and software wallets. However ECDH addresses do not solve all privacy problems as they are still vulnerable to mystery shopper payments ; an adversary can donate some bitcoins and watch on the blockchain to see where they go afterwards, using heuristics like the common-input-ownership heuristic to obtain more information such as donation volume and final destination of funds. Retrieved 16 March Archived PDF from the original on 14 October High price volatility and transaction fees make paying for small retail purchases with bitcoin impractical, according to economist Kim Grauer. An official investigation into bitcoin traders was reported in May Much research has gone into improving the privacy of scripts by finding ways to make several different script kinds look the same. Archived from the original on 5 December
Say that the adversary knows that Mr. Martin's Press. It allows for any number of entities to between them create a so-called proposed transaction graph PTG which is a list of connected transactions. However, each new idea brings us closer to a world where the transfer of important information is fast, easy and free! Bitcoin Recruits Snap To". Certainly its privacy is better than the privacy of on-chain transactions. Retrieved 23 December Retrieved 10 June Full talk: Breaking Bitcoin conference. Only in a perfectly enlightened discrimination free world where no one has undue authority over anyone else could we retain our dignity and make our lawful transactions freely without self-censorship if we don't have privacy. Retrieved 17 January Retrieved 18 September Confidential transactions CT is a cryptographic protocol which results in the amount value of a transaction being encrypted. The full node is run entirely over Tor to stop your internet service provider or any network-level adversary from seeing that you run a bitcoin node. The employer also can't correlate the amounts, because they see you deposit 0. Others have been implemented in some open source projects or services, which may use more than one technique at a time. Other scripts are possible with the most common being multisignature.
Retrieved 14 January Lecture Notes in Computer Science, vol Some very old software from the era metatrader 4 linux vps pairs trading options in tos did not have Deterministic wallets did not use a new address change but sent the change back to the input address. Prices are not usually quoted in units of bitcoin and many trades involve one, or sometimes two, conversions into conventional currencies. This is also possible if the inputs are of mixed types created by wallets supporting multiple script types for backwards compatibility. Archived from the original on 27 February Per researchers, "there is little sign of bitcoin use" in international remittances despite high fees charged by banks and Western Union who compete vanguard total world stock index etf fact sheet arrow financial stock dividend this market. Is it better than Bitcoin or a lame rip-off? This transaction breaks the common-input-ownership heuristicbecause its inputs are not all owned by the same person but it is still easy to tell where the bitcoins of each input ended up. Retrieved 11 July Many lightweight wallets use the BIP37 standard, which has serious design flaws leading to privacy leaks. This doesn't mean the onion routing used by Lightning Network is useless, far from it, but the privacy is not as strong as with Tor. If a connection-controlling adversary is a concern, then bitcoin can be run entirely over tor.
Stellar Lumens: The Stellar Coin. This section discusses at the money options strategy day trading stock simulator tradingsim methods an adversary may use for analyzing fxopen mt4 mac institute mobile al public blockchain. Retrieved 14 January Archived from the original on 6 October If you give up your delivery address which you'll have to if you're buying physical goods online then that will be a data leak. Archived from the original on 7 February The exact value for "how slowly" a cluster is allowed to grow is an open question. Other branches would only be used where some participant is failing to cooperate. You cannot compete effectively if your competition is tracking your sales. In the long term as bitcoin miner fees go up, resource-costly privacy technologies will be priced out and replaced by resource-efficient ones. It's 'the Harlem Shake of currency ' ". ECDH addresses can be used to improve privacy by helping avoid address reuse. The receiver of the first bitcoin transaction was cypherpunk Hal Finneywho had created the first reusable proof-of-work system RPoW in Price, [j] semilogarithmic plot. Some economists, including several Nobel laureateshave characterized it as a speculative bubble. Bitcoin Cash Bitcoin Gold.
How Can it be Abused? New York. Lessons from the failure of BIP37 can be useful when designing and understanding other privacy solutions, especially with the point about data fusion of combining BIP37 bloom filter leaks with blockchain transaction information leaks. Encyclopedia of Physical Bitcoins and Crypto-Currencies. An adversary able to snoop on your internet connection such as your government, ISP, Wifi provider or VPN provider can see data sent and received by your node. Transactions are many-to-many mappings, so in a very important sense it's impossible to answer the question of where the 1 btc ended up. An example might be because the wallets want to consolidate inputs in times of cheap miner fees. Here's how he describes it". See also the privacy examples for real-life case-studies. Shiller writes that bitcoin has potential as a unit of account for measuring the relative value of goods, as with Chile's Unidad de Fomento , but that "Bitcoin in its present form [ A1, A2, etc refer to output addresses of those transactions. Retrieved 22 December
Retrieved 10 December BIP defines a mechanism for replacing an unconfirmed transaction with another transaction that pays a higher fee. The market is becoming very crowded with Bitcoin fork coins and only the ones with the best protocols will succeed. Retrieved 11 January The analyst would then ignore or exclude some of these possibilities. This computation can be done in a split second. This is similar to other internet phenomena like Craigslist which organize meetups for exchange. In the PTG the bitcoins belonging to the entities are sent to and fro in all the transactions, but at the end of the PTG they are all returned to their rightful owners. It would be a serious privacy leak if the change address can be somehow found, as it would link the ownership of the now spent inputs with a new output. The recipient can look at the transaction on the blockchain and deduce that the sender owned at least 10 bitcoins. Retrieved 18 September Privacy-Enhancing Overlays in Bitcoin. Justice Department launched an investigation into possible price manipulation, including the techniques of spoofing and wash trades. Retrieved 14 April It works by batching up several payments into one block chain transaction.
Put in the simplest terms, the quest for decentralised trust has quickly become an environmental disaster. Some lightweight wallets also run entirely td ameritrade investment newsletters high tech companies stock tor. It is similar to a cash-in-person trade but the traders never meet up. However within that security model you get excellent of privacy, and the sidechain itself is marketed towards traders and hedgers who certainly want to keep their trading activities private to stop other traders front-running. Retrieved 26 March Units of the bitcoin currency are not watermarked within a transaction in other words they don't tradingview crypto strategies ninjatrader 8 custom indicator strategy little serial numbers. Archived from the original on 3 November CBS DC. On the other hand, here is an example of somebody using bitcoin to make a donation that is completely anonymous. This reveals the change address exactly. Physical wallets store the credentials necessary to spend bitcoins offline and can be as simple as a paper printout of the private key: [7] : ch. Obviously Alice and Bob generate new addresses each to avoid the privacy loss due to address reuse. Archived from the original on 16 June Digital forensics is one reason why all good wallet software encrypts wallet files, although that can exchanges supporting anonymous bitcoin fork coinbase create paper wallet beaten if a weak encryption password is used. Concerns about bitcoin's environmental impact relate bitcoin's energy consumption to carbon emissions. A1, A2, etc refer to output addresses of those transactions. Retrieved 23 January Users should check with their local postal service if there are any guidelines around sending cash-by-mail. Archived PDF from the original on 10 April Money portal. Navigation menu Personal tools Create account Log in. Best blockchain stocks fidelity brokerage 500 free trades on 20 April For example, it may find wallet cluster A belonging to Alice and another wallet cluster B belonging to Bob.
As an example, consider five typical transactions that consume one input each and produce two outputs. Sometimes users may voluntarily reveal data about themselves, or be required to by the entity they interact with. It is hoped one day there may be work done to make this easier, but as all development is done by volunteers there can be no roadmap for this. This is a heuristic or assumption which says that if a transaction has more than one input then all those inputs are owned by the same entity. Some wallet software handles change in a very un-private way. This has the most effect on early adopters of new wallet technology, like p2sh or segwit. A solution is rendez-vous routing [81] [82] , also called Hidden Destinations [83] , which allow Lightning payments to be sent from a source node to destination node without either the source or destination needing to reveal their nodes and associated information. Archived from the original on 12 October A paper wallet is created with a keypair generated on a computer with no internet connection ; the private key is written or printed onto the paper [h] and then erased from the computer. For example, when intending to send 1 bitcoins to somebody a user may only have an input worth 10 bitcoins. Off-chain transactions refer to any technology which allows bitcoin transactions on a layer above the blockchain. Avoiding address reuse is like throwing away a pseudonym after its been used.
That server can easily spy on the wallet. As of the beginning ofcoinjoins happen approximately once every hour and a stoneglow candles trade macd option snipper. Samourai Wallet is a smartphone wallet which implements some privacy features. This may work well in a freelancing or contracting setting. Chronic deflation may keep Bitcoin from displacing its rivals". Archived from the original on 11 January Archived from the original on 4 July Very similar sell price bitcoin bittrex buy sell api the previous example, but more than one address and transaction is used. Retrieved 14 April Retrieved 9 November See also: Fork blockchain and List of bitcoin forks. Retrieved 23 December However, in my opinion, the price of Bitcoin Diamond will have to be more stable before it attracts any big-brand clients like Starbucks or McDonalds. This is an old method for breaking the transaction graph. This kind of wallet has no privacy at all, the operating company can see all the user's addresses and all their transactions, most of the time they'll see the user's IP address. Andresen later became lead developer at the Bitcoin Foundation. Archived from the original on 24 June seding btc from coinbase bitpay recurring payments There is some nuance - in certain situations bitcoin can be very private. European Banking Authority. CNN Tech. Retrieved 17 February Archived from the original on 20 October

Main article: BIP37 privacy problems. Retrieved 30 July It is therefore unclear whether ECDH are useful outside the use-case of non-interactive donations or a self-contained application which sends money to one destination without any interactivity. The scheme is much more expensive in terms of computation, but it may still be practical. To claim the reward, a special transaction called a coinbase is included with the processed payments. Off-chain transactions refer to any technology which allows bitcoin transactions on a layer above the blockchain. An equal-output CoinJoin hides the source and destination of auto fibonacci retracements thinkorswim dragonfly doji in downtrend certain coin, but the structure of the transactions reveals that something is being hidden. Hugosway forex review stock trading risk management strategy template Economics Legal status. American Bar Association. It doesn't serve any socially useful function. Globe and Mail. The Bitcoin protocol was their gift to the world. This is why even leaks of a small amount of information should be avoided, as they can often completely ruin privacy when combined with other leaks. Without privacy malicious parties have more ability to steal your identity, snatch your large purchases off your doorstep, or impersonate businesses you transact with towards you
As of late CoinJoin is the only decentralized bitcoin privacy method that has been deployed. For broader coverage of this topic, see Mining pool. Retrieved 3 July For example, for a transaction with 1 input spending a p2pkh coin and creating 2 outputs, one of p2pkh and one of p2sh, it is very likely that the p2pkh output is the change while the p2sh one is the payment. Avoiding address reuse is like throwing away a pseudonym after its been used. Most importantly, financial privacy isn't incompatible with things like law enforcement or transparency. As they are undetectable we wouldn't even know whether they are being used today. JoinMarket can interface with a Bitcoin Core full node in order to privately obtain the history of its own wallet. Moreover, the number of valid private keys is so vast that it is extremely unlikely someone will compute a key-pair that is already in use and has funds. There is at least one situation where this happened.
There are several implementations of Lightning Network as of early; such as LND , c-lightning , eclair , etc. Retrieved 19 April If someone uses their exchanger to buy bitcoins and then transacts the coins to the trap website, the block chain would show:. Save my name, email, and website in this browser for the next time I comment. Alone, this information can't identify anyone because the addresses and transaction IDs are just random numbers. This is very bad for privacy as the website can easily link the user's IP address to their bitcoin transaction unless tor is used , and the queries to their website reveal that the transaction or address is of interest to somebody who has certain behavioural patterns. The Commodity Futures Trading Commission then subpoenaed the data from the exchanges. Steganographic encryption of a message can be done by embedding an encrypted message into an audio file or image which hides the message in the noise. Washington Post. The adversary hopes that users or their wallet software will use the payments as inputs to a larger transaction which will reveal other addresses via the the common-input-ownership heuristic. Regulations and bans that apply to bitcoin probably extend to similar cryptocurrency systems. Off-Chain Transactions are one way to avoid this trade-off between privacy and scalability. Jump to: navigation , search. Dandelion is another technology for private transaction broadcasting.